The Importance of Multi-Factor Authentication: Implementation Tips
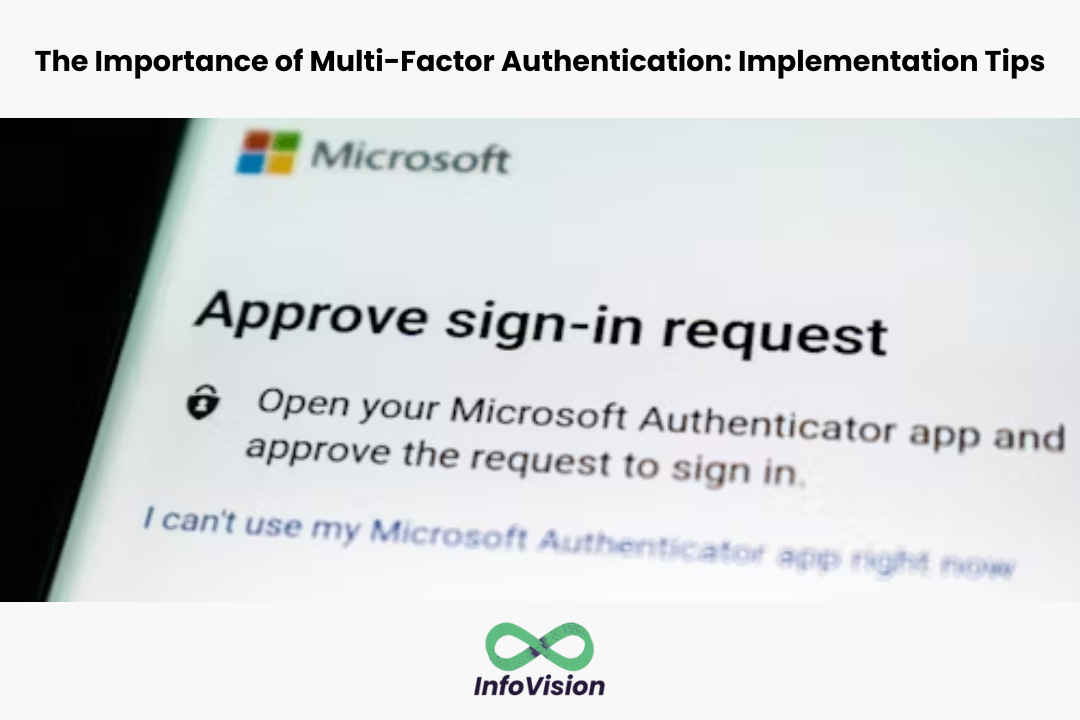
Multi-factor authentication (MFA) is a security measure that requires users to provide two or more forms of identification before accessing a system or application. It is an essential tool for protecting sensitive data and preventing unauthorized access. With the increasing number of cyber-attacks, MFA has become a critical security measure for individuals and businesses alike.
The importance of MFA cannot be overstated. Passwords can be easily compromised, and cybercriminals are becoming more sophisticated in their methods. MFA adds an extra layer of security, making it much more difficult for hackers to gain access to sensitive information. By requiring multiple forms of identification, MFA reduces the risk of identity theft, data breaches, and financial fraud. In fact, according to a report by Microsoft, MFA can block over 99.9% of account compromise attacks.
Understanding Multi-Factor Authentication
Definition and Key Concepts
Multi-factor authentication (MFA) is a security system that requires users to authenticate their identity using two or more different factors. The goal of MFA is to make it harder for an attacker to gain unauthorized access to a user’s account or sensitive information.
The most common factors used in MFA are:
- Something you know, such as a password or PIN
- Something you have, such as a smart card or security token
- Something you are, such as a fingerprint or facial recognition
By requiring multiple factors, MFA provides an additional layer of security beyond traditional username and password authentication. Even if an attacker is able to obtain a user’s password, they would still need the other factors to gain access.
Types of Authentication Factors
There are many types of authentication factors that can be used in MFA. Some common examples include:
- Passwords or PINs
- Security tokens or smart cards
- Biometric factors, such as fingerprints or facial recognition
- One-time passwords (OTPs) generated by a mobile app or hardware token
- Location-based factors, such as IP address or geolocation
Each factor has its own strengths and weaknesses, and the best approach will depend on the specific use case. For example, biometric factors can be very secure but may not be practical in all situations. Similarly, OTPs can provide strong security but may be inconvenient for users to use.
Overall, MFA is an important tool for protecting against unauthorized access to sensitive information. By requiring multiple factors for authentication, MFA can help prevent many types of attacks and keep users’ information secure.
The Necessity of Multi-Factor Authentication
Multi-Factor Authentication (MFA) is a security measure that requires users to provide two or more forms of identification to access an account or system. This method of authentication has become increasingly necessary due to the rising cybersecurity threats that individuals and organizations face on a daily basis.
Rising Cybersecurity Threats
With the increasing use of technology, cyber threats have become more sophisticated, making it easier for hackers to gain unauthorized access to personal and sensitive information. In 2020, the FBI reported receiving 2,047 complaints related to ransomware attacks, resulting in a loss of $29.1 million to victims. These numbers highlight the importance of implementing MFA to protect against such attacks.
Benefits Over Single-Factor Authentication
MFA offers several benefits over single-factor authentication, which only requires users to provide one form of identification, usually a password. The use of MFA makes it significantly harder for hackers to gain access to an account or system, as they would need to have access to multiple factors of authentication. This reduces the likelihood of successful attacks and helps to keep sensitive information secure.
In addition, MFA can also help to prevent phishing attacks, which are a common method used by hackers to gain access to accounts. With MFA, even if a user provides their login credentials to a phishing website, the hacker would still need to provide the additional factor of authentication, making it significantly harder for them to gain access.
Overall, the necessity of Multi-Factor Authentication cannot be overstated. Its benefits over single-factor authentication make it an essential security measure for individuals and organizations alike.
Regulatory Compliance and MFA
Multi-factor authentication (MFA) is becoming a necessity for achieving and maintaining compliance with industry regulations. Implementing MFA significantly reduces the risk of system penetration, up to a remarkable 99%. This is because MFA requires users to present a combination of two or more credentials to verify their identity for login, making it difficult for unauthorized users to gain access to sensitive data.
Industry Regulations Requiring MFA
Several industry regulations require the use of MFA to ensure the security of sensitive data. For example, the Payment Card Industry Data Security Standard (PCI-DSS) requires MFA to be implemented in certain situations to protect credit card information. The Health Insurance Portability and Accountability Act (HIPAA) also requires MFA to be used to secure electronic protected health information (ePHI).
Data Protection Laws
Data protection laws are becoming more stringent, and MFA is often a key requirement for achieving compliance. For example, the General Data Protection Regulation (GDPR) requires organizations to implement appropriate technical and organizational measures to ensure the security of personal data. MFA is one of the recommended measures to achieve compliance with GDPR.
In conclusion, implementing MFA is essential for achieving and maintaining compliance with industry regulations and data protection laws. Organizations should consider implementing MFA to increase the security of their sensitive data and protect against unauthorized access.
Planning Your MFA Implementation
Implementing multi-factor authentication (MFA) can be a complex process, but it is crucial for securing your organization’s sensitive data and preventing cyber attacks. To ensure a successful MFA deployment, it is essential to plan and prepare accordingly. This section will provide guidance on how to plan your MFA implementation.
Assessing Your Security Needs
Before selecting an MFA solution, it is important to assess your organization’s security needs. This includes identifying the assets and data that need to be protected, as well as the potential risks and threats that your organization may face. A risk assessment can help you determine the level of security required for each asset and data type.
Once you have identified your security needs, you can then evaluate the different MFA solutions available to determine which one is best suited for your organization.
Selecting the Right MFA Solution
When selecting an MFA solution, it is important to consider factors such as ease of use, cost, and compatibility with your existing systems. There are various types of MFA solutions available, including hardware tokens, software tokens, and biometric authentication.
Hardware tokens are physical devices that generate one-time passcodes (OTPs) that are used for authentication. Software tokens are applications that run on mobile devices or computers and generate OTPs. Biometric authentication uses unique physical characteristics, such as fingerprints or facial recognition, to verify a user’s identity.
It is important to choose an MFA solution that is easy for your users to use and does not disrupt their workflow. Additionally, the solution should be cost-effective and compatible with your existing systems.
By carefully assessing your security needs and selecting the right MFA solution, you can ensure a successful implementation and protect your organization’s sensitive data from cyber threats.
Technical Aspects of MFA
Multi-Factor Authentication (MFA) is a security mechanism that requires users to provide two or more forms of authentication to gain access to a system or application. MFA provides an additional layer of security beyond the traditional username and password combination, making it more difficult for hackers to gain unauthorized access.
Token-Based Methods
One of the most common forms of MFA is token-based authentication. In this method, the user is provided with a physical or virtual token that generates a one-time password (OTP) that is valid for a limited time. The user must enter this OTP along with their username and password to gain access to the system or application. The physical token can be in the form of a key fob or a smart card, while the virtual token can be generated using an app on the user’s smartphone.
Biometric Verification
Biometric verification is another form of MFA that is becoming increasingly popular. Biometric authentication uses a person’s unique physical characteristics, such as fingerprints, facial recognition, or iris scans, to verify their identity. Biometric authentication is more secure than traditional passwords because it is much harder to replicate a person’s biometric data than it is to guess or steal a password.
Mobile Authentication Apps
Mobile authentication apps are another form of MFA that is gaining popularity. These apps generate a one-time password (OTP) that the user must enter along with their username and password to gain access to the system or application. The OTP is generated on the user’s smartphone and is valid for a limited time. Mobile authentication apps are convenient because the user always has their smartphone with them, and the app can be easily downloaded and installed.
In conclusion, token-based methods, biometric verification, and mobile authentication apps are all effective ways to implement MFA. Organizations should carefully consider which method is best suited for their needs and implement MFA to enhance their security posture.
User Experience and MFA
Multi-Factor Authentication (MFA) is an effective way of enhancing security for user accounts. However, implementing MFA can sometimes be viewed as an inconvenience by users. This section explores how to balance security and convenience while implementing MFA and the importance of user education and training.
Balancing Security and Convenience
One of the challenges of implementing MFA is finding the right balance between security and convenience. While MFA adds an extra layer of security, it can also make it more difficult for users to access their accounts. Therefore, it is important to choose an MFA solution that is both secure and easy to use.
Organizations can balance security and convenience by offering multiple MFA options. For example, users can choose to receive a text message with a one-time code or use a physical security key. This allows users to choose the option that best fits their needs and preferences.
User Education and Training
User education and training are critical when implementing MFA. Many users may not understand the importance of MFA or how to use it effectively. Therefore, it is important to provide clear instructions and training to users.
Organizations can provide user education and training through various methods such as online tutorials, webinars, and in-person training sessions. It is important to emphasize the importance of MFA and how it can protect user accounts from unauthorized access.
In addition, organizations can provide guidelines on how to choose strong passwords and avoid common security pitfalls such as phishing scams. By educating users on these topics, organizations can help users understand the importance of MFA and how to use it effectively.
Overall, balancing security and convenience and providing user education and training are critical when implementing MFA. By taking these steps, organizations can enhance security while ensuring that users can access their accounts easily and effectively.
MFA Integration Strategies
Implementing MFA can be a complex process, especially when it comes to integrating it into existing systems. However, there are several strategies that organizations can use to make the process smoother.
Incorporating MFA into Existing Systems
One of the most common strategies for integrating MFA into existing systems is to use a third-party identity provider (IdP) that supports MFA. This can provide a centralized location for managing user authentication across multiple systems and applications. Some popular IdPs that support MFA include Okta, Duo, and Microsoft Azure.
Another approach is to use MFA plugins or modules that are available for popular applications and systems. For example, many web servers and content management systems have plugins that can be used to add MFA support. These plugins can often be configured to work with a variety of MFA technologies, such as SMS-based codes, hardware tokens, or biometric authentication.
Cloud Services and MFA
Many cloud services, such as Amazon Web Services (AWS) and Google Cloud Platform (GCP), offer built-in support for MFA. This can make it easier to implement MFA for cloud-based applications and services. When using cloud services, it is important to ensure that MFA is enabled for all users and that appropriate policies are in place to enforce its use.
Organizations can also consider using cloud-based MFA services, such as Auth0 or Ping Identity. These services provide a centralized location for managing user authentication and can be used to secure both cloud-based and on-premises applications.
Overall, there are many strategies that organizations can use to integrate MFA into their systems and applications. By carefully considering the needs of their users and the security requirements of their systems, organizations can ensure that they implement MFA in a way that is effective and easy to use.
Best Practices for MFA Deployment
Multi-factor authentication (MFA) is a critical component of modern security practices. However, deploying MFA can be complex and require careful planning to ensure its effectiveness. In this section, we’ll outline some best practices for MFA deployment.
Policy Development
Before deploying MFA, it’s important to develop a clear policy that outlines the requirements and expectations for users. This policy should include guidelines for selecting authentication factors, such as passwords, smart cards, and biometrics. Additionally, it should specify the circumstances under which MFA is required, such as when accessing sensitive data or performing high-risk transactions.
To ensure that the MFA policy is effective, it should be reviewed and updated regularly. This can help to ensure that the policy remains relevant and that it addresses new threats and vulnerabilities as they arise.
Testing and Feedback Loops
Deploying MFA requires careful testing to ensure that it is effective and that it doesn’t create unnecessary friction for users. This testing should include both technical testing and user testing to identify any issues or areas for improvement.
To ensure that MFA is effective, it’s important to establish feedback loops that allow users to report issues and provide feedback. This feedback can be used to improve the MFA system and ensure that it meets the needs of users while providing the necessary level of security.
Overall, deploying MFA requires careful planning and attention to detail. By following these best practices, organizations can ensure that their MFA system is effective, user-friendly, and provides the necessary level of security to protect against modern threats.
Handling MFA Challenges
Implementing Multi-Factor Authentication (MFA) can be challenging, especially when it comes to dealing with user resistance and ensuring recovery and backup methods are in place. In this section, we will discuss these challenges and provide some guidance on how to handle them.
Dealing with User Resistance
One of the biggest challenges when implementing MFA is getting users on board. Many users find MFA to be an inconvenience and may resist using it. To overcome this challenge, it is important to communicate the benefits of MFA to users, such as increased security and protection against unauthorized access. Additionally, providing training and support can help users understand how to use MFA and address any concerns they may have.
Another way to deal with user resistance is to make the MFA process as seamless as possible. For example, using push notifications or biometric authentication can make the process faster and more user-friendly.
Recovery and Backup Methods
Another challenge of implementing MFA is ensuring recovery and backup methods are in place. In the event that a user loses their device or is unable to access their MFA method, there needs to be a backup plan in place to ensure they can still access their accounts.
One way to address this challenge is to provide multiple MFA methods, such as SMS, email, or a backup code. Additionally, having a recovery plan in place, such as a password reset process, can help users regain access to their accounts in case of an emergency.
It is important to note that while MFA can provide increased security, it is not foolproof. Therefore, having a backup plan in place is crucial to ensure that users can still access their accounts in case of any issues with their MFA method.
Monitoring and Maintaining MFA Systems
Once Multi-Factor Authentication (MFA) has been implemented, it is crucial to monitor and maintain the system to ensure its effectiveness. This section will discuss two important aspects of monitoring and maintaining MFA systems: Regular Audits and Updates and Incident Response Planning.
Regular Audits and Updates
Regular audits and updates are essential to ensure that the MFA system is functioning correctly and is up-to-date with the latest security patches. It is recommended to perform regular audits of the MFA system to identify any vulnerabilities that could be exploited by attackers. The audit should include a review of the MFA configuration, policies, and procedures to ensure that they are in line with the organization’s security requirements.
It is also important to keep the MFA system up-to-date with the latest security patches and updates. This will ensure that any known vulnerabilities are addressed promptly, reducing the risk of a successful attack. The MFA system should be configured to receive automatic updates, and the IT team should monitor the system to ensure that updates are applied promptly.
Incident Response Planning
Despite the best efforts of an organization, there is always a risk that a security breach could occur. Therefore, it is essential to have an incident response plan in place to address any security incidents promptly. The incident response plan should include procedures for detecting, analyzing, and responding to security incidents.
The incident response plan should also include procedures for responding to MFA-related incidents. For example, if an MFA token is lost or stolen, the incident response plan should include procedures for revoking the token and issuing a new one. The incident response plan should also include procedures for investigating any MFA-related incidents to identify the cause and prevent future incidents.
In conclusion, monitoring and maintaining MFA systems is essential to ensure their effectiveness and reduce the risk of a security breach. Regular audits and updates and incident response planning are two critical aspects of monitoring and maintaining MFA systems that organizations should prioritize.
Frequently Asked Questions
What are the benefits of using multi-factor authentication in an organization?
Multi-factor authentication (MFA) provides an additional layer of security to protect against unauthorized access to sensitive information. By requiring users to provide more than one form of identification, MFA makes it more difficult for hackers to gain access to important data. This added layer of security can help prevent data breaches, which can be costly and damaging to an organization.
How does multi-factor authentication enhance cybersecurity measures?
MFA enhances cybersecurity measures by requiring users to provide more than one form of identification before granting access to sensitive information. This makes it more difficult for hackers to gain access to important data. Additionally, MFA can help prevent phishing attacks, where a hacker attempts to gain access to sensitive information by tricking the user into providing their login credentials. By requiring an additional form of identification, MFA can prevent these types of attacks.
What are some common methods of multi-factor authentication currently in use?
Some common methods of MFA currently in use include biometric authentication, such as fingerprint or facial recognition, hardware tokens, such as USB keys, and one-time passwords sent via text message or email. Each method has its own benefits and drawbacks, and organizations should choose the method that best fits their needs.
How can businesses effectively implement multi-factor authentication for their systems?
To effectively implement MFA for their systems, businesses should start by conducting a risk assessment to identify areas where MFA is needed. They should then choose a method of MFA that best fits their needs and ensure that it is properly configured. It is also important to educate users on the importance of MFA and how to use it effectively.
In what ways does multi-factor authentication contribute to securing online banking transactions?
MFA contributes to securing online banking transactions by requiring users to provide an additional form of identification before granting access to their accounts. This makes it more difficult for hackers to gain access to sensitive financial information, such as bank account numbers and credit card information.
What steps should be taken to integrate multi-factor authentication into existing security infrastructure?
To integrate MFA into existing security infrastructure, businesses should start by conducting a risk assessment to identify areas where MFA is needed. They should then choose a method of MFA that best fits their needs and ensure that it is properly configured. It is also important to educate users on the importance of MFA and how to use it effectively. Finally, businesses should monitor their systems to ensure that MFA is being used effectively and make any necessary adjustments.